This Writeup describes the process I followed to complete Memory Forensics room TryHackMe platform.
This room, as it’s name suggests, about forensics to some windows memory images. This is an easy room, and it’s aimed for getting a first approach with memory forensics and volatility fundamentals in my point of view.
Task 1
This task just give us an introduction to the room, and post some interesting links, aimed to help to solve the room with the volatility tool.
Task 2
In this task we are given with an image from a windows machine, aimed to get John’s password, we can firstly analyze the image by using the “imageinfo” option from the volatility tool. We get the following:
$ volatility -f login.vmem imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/home/kali/login.vmem)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf80002c4a0a0L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80002c4bd00L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2020-12-27 06:20:05 UTC+0000
Image local date and time : 2020-12-26 22:20:05 -0800
From the previous output we can use any of the profiles given for further process. I chose the first one and ran the “hivelist” command from volatility which give us the list of hives located in the windows machine:
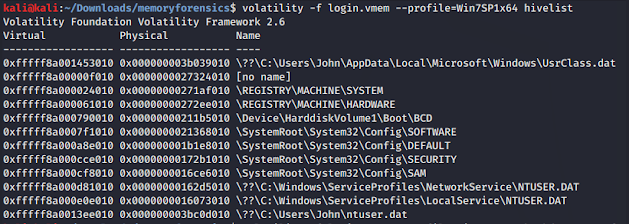
$ volatility -f login.vmem --profile=Win7SP1x64 hivelistVolatility Foundation Volatility Framework 2.6
Virtual Physical Name
------------------ ------------------ ----
0xfffff8a001453010 0x000000003b039010 \??\C:\Users\John\AppData\Local\Microsoft\Windows\UsrClass.dat
0xfffff8a00000f010 0x00000
00027324010 [no name]
0xfffff8a000024010 0x00000000271af010 \REGISTRY\MACHINE\SYSTEM
0xfffff8a000061010 0x00000000272ee010 \REGISTRY\MACHINE\HARDWARE
0xfffff8a000790010 0x00000000211b5010 \Device\HarddiskVolume1\Boot\BCD
0xfffff8a0007f1010 0x0000000021368010 \SystemRoot\System32\Config\SOFTWARE
0xfffff8a000a8e010 0x000000001b1e8010 \SystemRoot\System32\Config\DEFAULT
0xfffff8a000cce010 0x00000000172b1010 \SystemRoot\System32\Config\SECURITY
0xfffff8a000cf8010 0x0000000016ce6010 \SystemRoot\System32\Config\SAM
0xfffff8a000d81010 0x00000000162d5010 \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT
0xfffff8a000e0e010 0x0000000016073010 \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT
0xfffff8a0013ee010 0x000000003bc0d010 \??\C:\Users\John\ntuser.dat
Now, as we can see, last command listed us some hives. The password from the current user is stored in “SAM” hive, and configuration and other system information in the “SYSTEM” hive.
Knowing this, we are interested in get the password hashes stored in , for which we will dump its contents, with the “hashdump” volatility option in the memory address that correspond to those hives, as follows:
$ volatility -f login.vmem --profile=Win7SP1x64 hashdump -y 0xfffff8a000cf8010 0xfffff8a000024010
Volatility Foundation Volatility Framework 2.6
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
John:1001:aad3b435b51404eeaad3b435b51404ee:*****[EDITED]*****:::
HomeGroupUser$:1002:aad3b435b51404eeaad3b435b51404ee:91c34c06b7988e216c3bfeb9530cabfb:::
We can use any cracker to get John’s password, there are a lot out there, for example “John the Ripper” and “hashcat“. In this case, I’ll use an online cracker called CrackStation. We’ll use the obtained hash password and we’ll get Jonh’s plain text password:
At this point we got the first answer.
Task 3
In this case, we are given with another memory image and we are aimed to get the last shutdown time and get the text John wrote in some place, but as we can see in the image of the task we might think it was written in the command prompt.
First, we get the profiles with the “imageinfo” option as last time:
$ volatility -f analysis.vmem imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/home/kali/analysis.vmem)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf80002bfd0a0L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80002bfed00L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2020-12-27 23:06:01 UTC+0000
Image local date and time : 2020-12-28 00:06:01 +0100
Using the help menu, we can see that we have a “shutdowntime” option from volatility, which in fact after testing with first suggested profile gave us the last shutdown time:
$ volatility -f analysis.vmem --profile=Win7SP1x64 shutdowntime
Volatility Foundation Volatility Framework 2.6
Registry: SYSTEM
Key Path: ControlSet001\Control\Windows
Key Last updated: 2020-12-27 22:50:12 UTC+0000
Value Name: ShutdownTime
Value: *****[EDITED]***** UTC+0000
Now, we need to find what did John write, for that checking the help menu again, we can see that there is a cmdscan command which as per volatility documentation
The cmdscan plugin searches the memory of csrss.exe on XP/2003/Vista/2008 and conhost.exe on Windows 7 for commands that attackers entered through a console shell (cmd.exe).
https://github.com/volatilityfoundation/volatility/wiki/Command-Reference#cmdscan
Executing this command for first suggested profile we cat get the next answer:
$ volatility -f analysis.vmem --profile=Win7SP1x64 cmdscan
Volatility Foundation Volatility Framework 2.6
**************************************************
CommandProcess: conhost.exe Pid: 2488
CommandHistory: 0x21e9c0 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 7 LastAdded: 6 LastDisplayed: 6
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
Cmd #0 @ 0x1fe3a0: cd /
Cmd #1 @ 0x1f78b0: echo THM{*****[EDITED]*****} > test.txt
Cmd #2 @ 0x21dcf0: cls
Cmd #3 @ 0x1fe3c0: cd /Users
Cmd #4 @ 0x1fe3e0: cd /John
Cmd #5 @ 0x21db30: dir
Cmd #6 @ 0x1fe400: cd John
Cmd #15 @ 0x1e0158: "
Cmd #16 @ 0x21db30: dir
Task 4
In this task, as in the previous ones, we are given with another memory image, we need to analyze it to get the passphrase used in “TrueCrypt” tool, so we first run “imageinfo” command:
$ volatility -f truecrypt.vmem imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/home/kali/truecrypt.vmem)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf80002c4d0a0L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80002c4ed00L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2020-12-27 13:41:31 UTC+0000
Image local date and time : 2020-12-27 05:41:31 -0800
After analyze the image we can select the first profile, then we can use the help menu searching for a module that might help us, and we can notice that there are a few “TrueCrypt” related commands.
We are interested in the one related with the passphrase, in this case “truecryptpassphrase“. After execute it we get the last answer:
$ volatility -f truecrypt.vmem --profile=Win7SP1x64 truecryptpassphrase
Volatility Foundation Volatility Framework 2.6
Found at 0xfffff8800512bee4 length 11: *****[EDITED]*****
As I said in the beginning of this write-up, this is an easy room. I hope this blog was useful and please wait for more write-ups.