SonarQube is an open source platform for continuous code quality inspection to perform automated reviews with static code analysis to detect code errors and security vulnerabilities. SonarQube offers reports on duplicate code, coding standards, unit tests, code coverage, code complexity, comments, bugs, and security vulnerabilities.
To run successfully SonarQube and analyze code we need two independent tools: SonarQube, which will run the server, and storage the results (backend); and SonarQube-cli, which will interact with the code and start the analysis.
The easiest way to install them is with docker container, you can find them in the following links:
Server
As I mentioned before, the easiest way to run SonarQube is with docker, just keep in mind it could be volatile and once it’s stopped all data will be removed. I’ll make the containers persistent.
Run SonarQube container:
docker run -d --rm --stop-timeout 3600 --name sonarqube -p 9000:9000 sonarqube:latest
You can find more parameters in official documentation.
You can verify if the container is running with docker ps or access to the web app http://localhost:9000/. The default credentials are admin:admin.
Now in the platform, we have to generate a token for the analysis. For that we go to: [user] > My account > Security > Generate Token. You will see something like in image below:
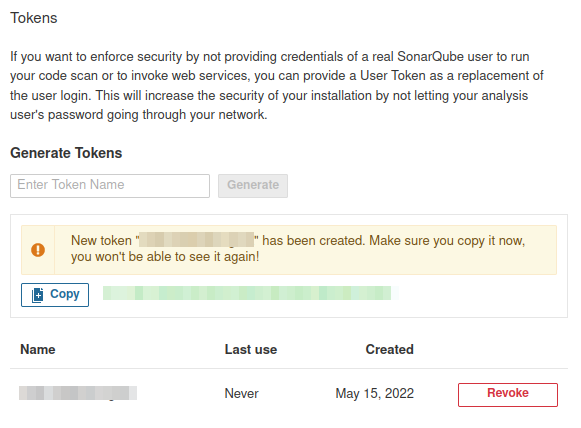 Generating new token.
Generating new token.
Don’t forget to copy the token.
CLI
Each project need to have a ‘sonar-project.properties‘ file, which will have parameters for the analysis, for example, server location, token, metadata, etc. It should be located in the source code root directory. You can find the full parameter list here.
I’ll be using an example source code provided by SonarQube, which you can find in this GitHub repository, and the following ‘sonar-project.properties‘ file:
sonar.projectKey=my:project
sonar.projectName=SonarQube Scanner Usage
sonar.projectVersion=1.0
sonar.qualitygate.wait=true
# Login
sonar.login=<token>
To start the scanning we can use the binary SonarQube-cli tool or the docker container.
You can download the binary tool from the SonarQube-cli link mentioned before. It’s a zip file which contains everything you need. You have to execute it from the source code directory:
./sonar-scanner-4.7.0.2747-linux/bin/sonar-scanner
Then just wait for the analysis to finish.
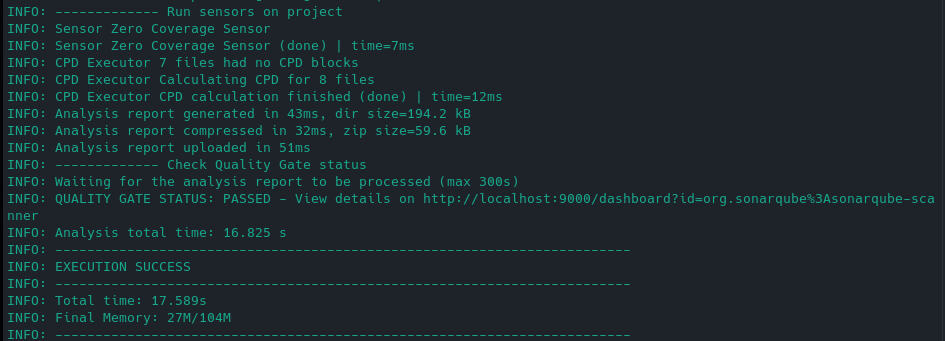 Running SonarQube scanner.
Running SonarQube scanner.
To use docker you just need to use the following command:
docker run --rm -v "$PWD:/usr/src" --network=host sonarsource/sonar-scanner-cli
You just can change the source directory ($PWD) as required.
Results
During the command execution we can see if the analysis was successful or not from the CLI, bur for further details we can go to the web platform, there we can see something like the following:
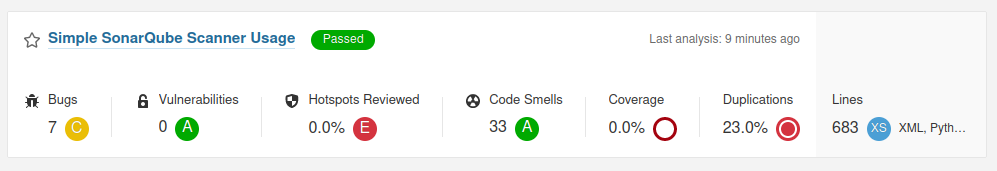 Scanning results.
Scanning results.
Walking around the results, you can find the issues with the code and even the recommendations to remediate.
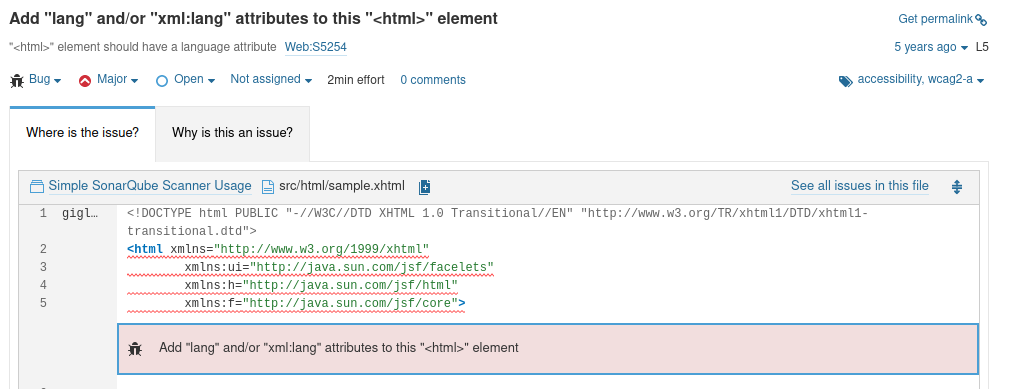 Code smell example.
Code smell example.
Maybe this seems to be too basic at the beginning, but with the right customization for the code analyzed, this would be too helpful to detect some bugs and other security issues in a very automatic way.