This entry is a Writeup of the process to solve Pickle Rick room from TryHackMe platform.
I can say that in this room we can learn different techniques to work with Linux environments when some commands are not available or we want to dive more in shell commands.
As per room description we have to exploit a webserver to find 3 ingredients that will help Rick make his potion to transform himself back into a human from a pickle.
As always the first thing we have to do is to enumerate the machine, we do this with nmap as follows:
$ nmap -sC -sV -T4 -p- 10.10.224.23
Starting Nmap 7.80 ( https://nmap.org ) at 2021-07-11 11:50 EDT
Warning: 10.10.224.23 giving up on port because retransmission cap hit (6).
Stats: 0:21:59 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 88.83% done; ETC: 12:15 (0:02:46 remaining)
Nmap scan report for 10.10.224.23
Host is up (0.20s latency).
Not shown: 65271 closed ports, 262 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 13:e0:f6:bc:e2:fa:36:a4:f2:4a:92:54:47:35:30:da (RSA)
| 256 1d:c9:76:45:f5:a6:8d:75:c8:6a:d7:da:bd:4f:90:90 (ECDSA)
|_ 256 83:72:57:08:99:1d:d6:6a:bd:9a:0a:95:f6:7d:dc:d0 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Rick is sup4r cool
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1513.53 seconds
We have two open ports, 22 and 80, at this stage we can’t use SSH because we don’t have any credentials. Anyways we can search any vulnerability on web page on port 80. We got the following image:
 Website on port 80.
Website on port 80.As we can see, it has no links to another page or any other detail at a first glance, so we can next enumerate for hidden directories or files, for this we can use gobuster, syntax is the following:
$ gobuster dir -u http://10.10.224.23/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.224.23/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
2021/07/11 12:48:11 Starting gobuster
===============================================================
/***REDACTED***.html (Status: 200)
/***REDACTED***.php (Status: 200)
/***REDACTED*** (Status: 301)
/***REDACTED***.php (Status: 302)
/***REDACTED***.txt (Status: 200)
As you can see, I enumerated using a wordlist looking for files with certain extension, which allowed us to get some results, some of them looks very interesting.
The most interesting show us a login portal for which we don’t have credentials.
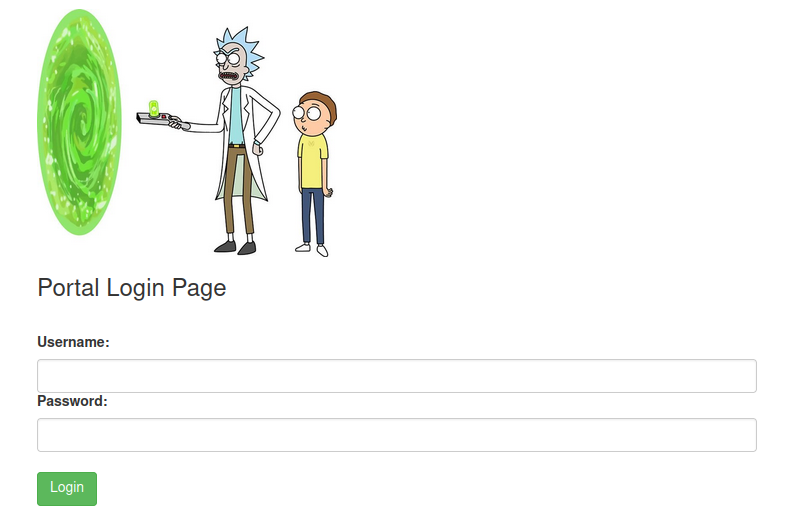 Login page.
Login page.We could try to brute force it, or find some credentials anywhere.
Fortunately for us, if we see the source code from the index page we got a username, we just need to get the password.
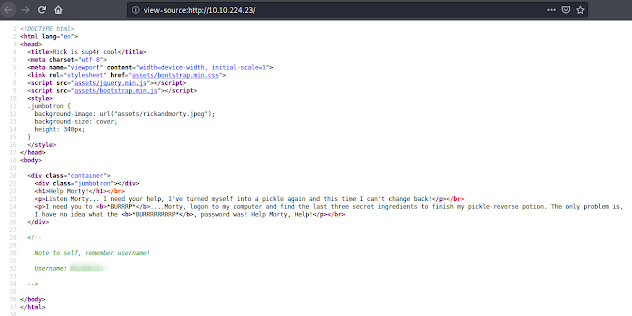 Index source code.
Index source code.Looking in the other found files, if we access to robots.txt, which sometimes has interesting information, we got some kind of word which could be used as a password.
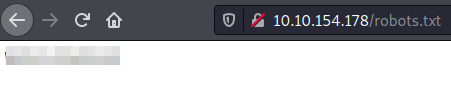 Reading robots.txt file.
Reading robots.txt file.We give it a try and we are inside.
We are given with a portal called “Command Panel”, which as tested is used to execute Linux commands, so we can try to find interesting files or try to execute any command.
 Listing files in present directory.
Listing files in present directory.First ingredient
After listing the files we got some text files, so we can try to read the clue file with cat command as usual.
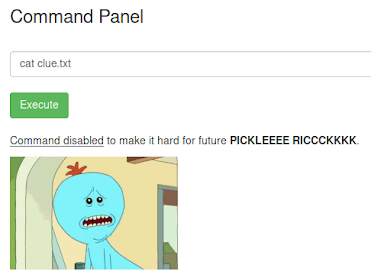 Error executing a command.
Error executing a command.As we can see in previous image, the cat command is disabled. However we can use any other command to read the file, for example less:
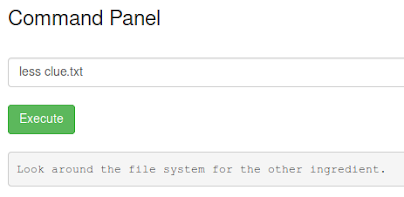 Reading clue file.
Reading clue file.We got it. We read the clue file which tell to look around in the system to get the needed ingredients. In the current folder we see the first one. We already know how to read the file:
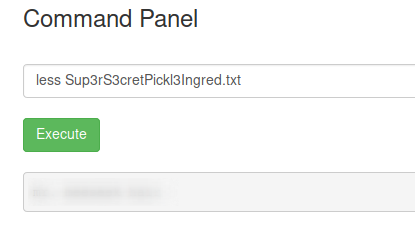 Reading first ingredient.
Reading first ingredient.Second ingredient
Looking around the system we got the Rick’s home directory in which we can find the secondary ingredient, as the same file name suggests, so we could try to read it as we have done before:
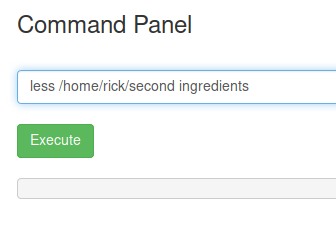 Trying to read second ingredients’ file.
Trying to read second ingredients’ file.We don’t get any output. This happens because we are trying to read a file whose name has 2 words and the shell is trying to read as argument the string till a space is found, I mean is like we had ran:
less /home/rick/second
File which doesn’t exist. Hence we have to options to take as just one argument the 2-words file name:
Using quotes around the file path:
less '/home/rick/second ingredients'
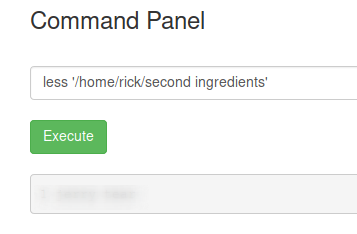 Reading first ingredient, method 1.
Reading first ingredient, method 1.
Escape the space with backslash character (“\”):
less /home/rick/second\ ingredients
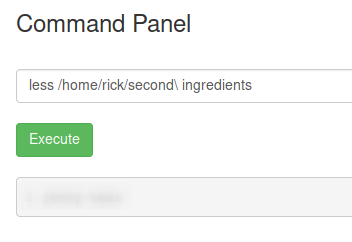 Reading second ingredient, method 2.
Reading second ingredient, method 2.
And there we have the second ingredient.
Third ingredient
If we try to look around in the system we might not be able to find the final ingredient. We need a way to escalate privileges as is highly possible the last file is owned by root.
If we list the sudo permissions of the current user we got the following:
We realize we can run any command with sudo permissions without password. So if we try to list files in the root directory (using sudo) in the root directory we see the following:
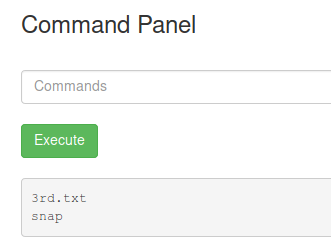 Listing files in the root directory.
Listing files in the root directory.Finally we can get the last ingredient, just need to run the command with sudo permissions, as follows:
Conclusions
As we could see in this room, even if we don’t have some commands available we could use alternative commands. Also is important to know that even if we don’t have a full-terminal we could still run Linux commands, in this room, for example, from the web browser itself.