This room is aimed to analyze a suspicious file was received in a phishing mail and we have to uncover the content (flag) in the attachment. In this writeup I’ll explain the process I followed to get the flag.
When we start the machine, we found two files in home directory. “MrPhisher.docm” is a document with the ability to run macros and the zip file has the same file but compressed.
 Files in home directory.
Files in home directory.
If we try to get open the file, we see the document indeed contain macros.
 Trying to ope suspicious file.
Trying to ope suspicious file.
To make easy the analysis and be able to download needed tools, I transferred the file to my local machine with netcat.
Local machine:
nc -nlvp <PORT> > MrPhisher.docm
Remote machine:
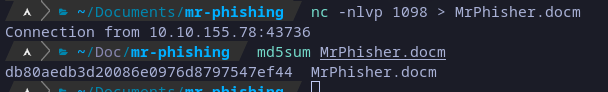 Setting listener and getting file.
Setting listener and getting file.
nc <IP> <PORT> < MyPhisher.docm
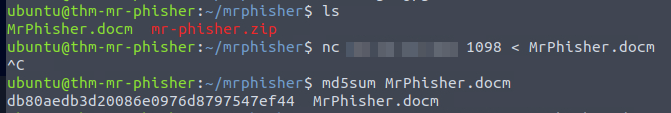 Sending file over netcat.
Sending file over netcat.
As a note, is important to verify the integrity of the transferred file, in previous images you can see I checked MD5 hash, and it’s the same.
Looking for ways to get the macros in this kind of files, I found oledump which can be downloaded here.
To see the streams of data, in which are contained to macros, we can just pass as an argument the file and we will get the following:
 Listing streams in file.
Listing streams in file.
We can see that “A3” and “A4” have and “M”, which means that streams are macros. So, it could be useful to get the contents in plain text. For that we can user the following commands:
oledump.py MrPhisher.docm -s A3 -v > NewMacros.txt
oledump.py MrPhisher.docm -s A4 -v > ThisDocument.txt
I saved the content in text files, where “-s” parameter selects the stream to dump and “-v” decompress VBA (Visual Basic for Applications) source code.
We can then see there is one interesting file “NewMacros.txt”, which have some kind of string in ASCII and then obfuscated with XOR:
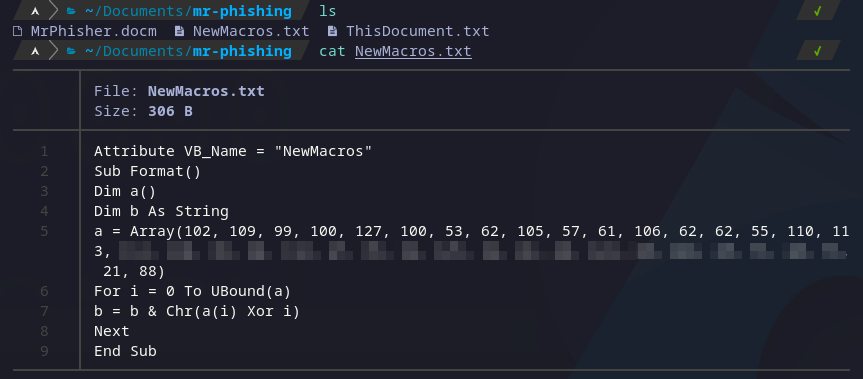 Reading macro.
Reading macro.
The code is easy to understand: we have and array of ASCII characters in decimal formal, then all elements are XOR with its index in the array. We can decode this with python by reversing the operations, the following script automates the process:
#!/usr/bin/python
a = [102, 109, 99, 100, 127, ..., 88]
flag = "".join(chr(i ^ idx) for idx, i in enumerate(a))
print(flag)
Finally, we can execute the file and get the flag.
 Getting flag.
Getting flag.